Infineon responds to encryption chip vulnerability
Researchers in the Czech Republic and the University of Cambridge identified risks with Infineon’s RSA encryption engine. The team found a vulnerability in generation of RSA keys used by a software library adopted in cryptographic smartcards, security tokens and other secure hardware chips made by Infineon.
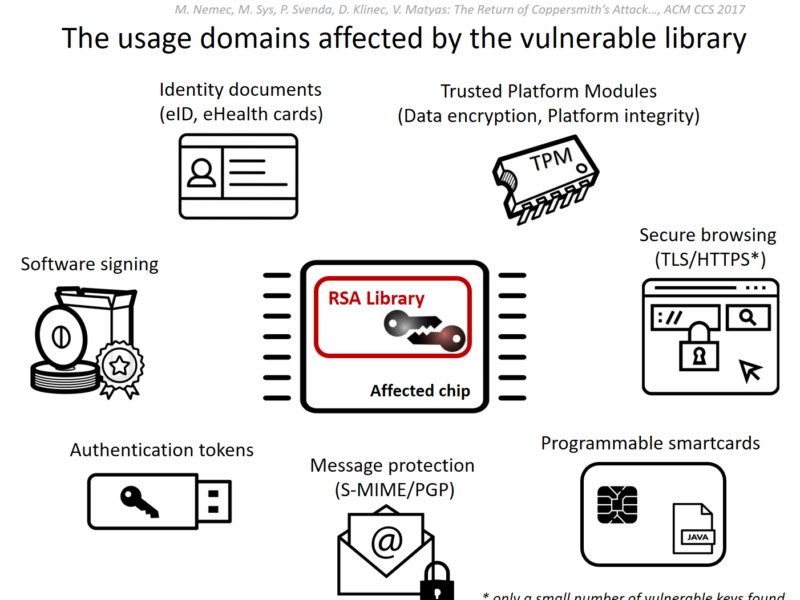
The attack discovered at the Centre for Research on Cryptography and Security (CRoCS) can crack commonly used key lengths, including 1024 and 2048 bits, with a reasonable amount of processing power, and affects chips manufactured as early as 2012, that are now commonplace. Major vendors including Microsoft, Google, HP, Lenovo, Fujitsu already released software updates.
“Researchers had informed Infineon in February 2017 how new advanced mathematical methods can be used to exploit the characteristics of acceleration algorithms. Such algorithms, used together with key generation, are software-based and not related to hardware,” said a spokesperson for Infineon.
“Infineon thoroughly investigated the newly developed methods and reacted immediately. To our knowledge, the software function is used for a very small proportion of security solutions that utilize our products. Our security chips themselves are not affected,” she said.
Infineon acknowledges that a potential weakness may occur in selected customers’ products that use the software function using the acceleration algorithm and the cryptographic keys have to be generated on the smart card itself. The function is seldom used but important for specific applications, such as digital signature applications with self-generated keys and TPMs (Trusted Platform Modules) mainly used in professional notebooks and to a lower share for professional desktop PCs.
“In close co-operation with the research team, our customers and the German certification body, the software function has been updated, evaluated, and is currently in the process of being certified and rolled out, including the production of new devices that use the new software function,” said Infineon. The details of the attack are at crocs.fi.muni.cz/public/papers/rsa_ccs17 and more details are set to be discussed at the ACM CCS 2017 security conference next week.
 If you enjoyed this article, you will like the following ones: don't miss them by subscribing to :
eeNews on Google News
If you enjoyed this article, you will like the following ones: don't miss them by subscribing to :
eeNews on Google News


