Analog IP tackles side channel attacks
Protecting against side channel attacks is a critical part of chip design, says Chris Morrison, director of product marketing at Agile Analog in Cambridge.
Researchers recently showed they can jailbreak an electric car using a voltage glitch as a side channel attack to give full access. This uses glitches on the voltage rail to force one or two bits to change to give access to the encryption keys and allowing hackers to potentially reprogramme the car.
“Some customers are really switched on, especially those working in aerospace and defence, but with others it varies massively,” Morrison tells eeNews Europe. “So many people are focussed on the data centre and high performance computing chip designs where side channel attacks are not a thing, but we are seeing more and more of it in automotive and the IoT where you have access to the equipment.”
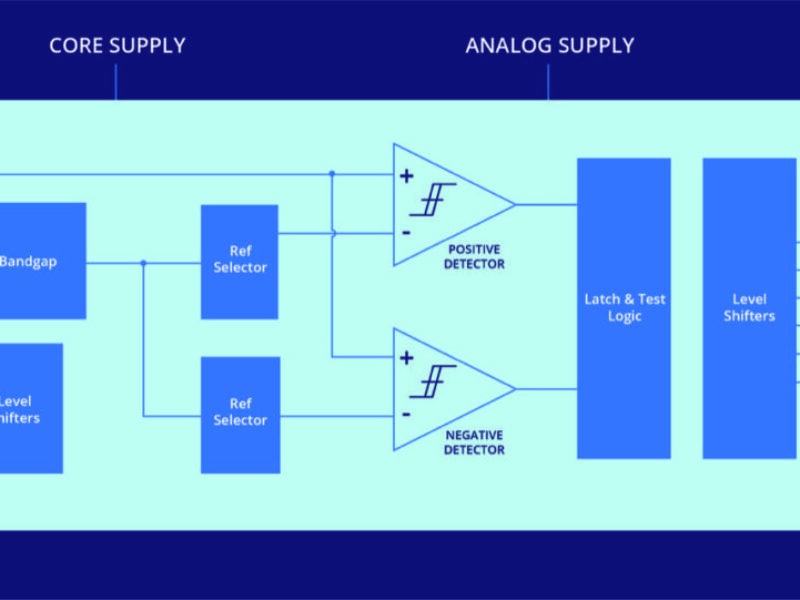
“This is something we know how to fix, but things are moving on in the technology. Three years ago we were protecting against glitches of 20ns, but the hackers have got better so our IP has to get better, we can now detect a 1ns glitch,” he said, “We’ve also added a clock glitch section with a reference block to compare the duty cycle, and you can use multiple clocks. We’ve also added temperature glitch protection.”
The move to more custom chips is driving more interest in these blocks.
“Particularly for the geopolitical situation there is a nervousness of buying in complete designs. You don’t have control over every designer that has been involved and that leaves you open to attacks,” said Morrison.
“On the flip side you have companies like NXP and Bosch who are so good at what they do, and when you have car makers starting their own chip companies it will be difficult for the first generation to replicate that level of capability. It’s hard to beat that experience.”
“Going vertically integrated ins great for us as a lot of traditional chip companies have so many of their own analog engineers and want to design their own chips. The vertically integrated companies have smaller design teams and so are looking to buy in more of their IP.”
Agile is already addressing these chi designers by supplying complete analog IP sub-systems for RISC-V chips. But protecting against side channel attacks requires more than just IP blocks.
“On the security side we want to do more than sell the IP. We want to support the customer rather than throw the IP over the wall. We can help by being the subject matter experts in security as we are in analog design,” he said.
“We are targeted with our security IP, we are not going to be playing with random number generators, physically unclonable functions or encryption. There’s a lot of companies out there doing that. What we want to do is specifically target the side channel attack area where we have differentiated IP while still working closely with the customer to cover all the bases and make sure that we don’t leave vulnerabilities,” he said.
- Joining Intel Foundry Services IP programme
- UltraSoC deal cybersecurity
- US intelligence VC investment
This comes from the customisation of the IP via the Composa tools developed by Agile,
“The amount of customisation we offer via the tool makes us an extension of the customer design team rather than an IP supplier,” said Morrison. “The voltage glitch uses a very fast comparator and we can have a fast ADC in there as well if the customer wants and that’s the kind of thigs that our tool is great at doing.”
Despite the small size of this part of the business, it is a key part of Agile’s strategy he says.
“It is a relatively small part of the business but security is one of the four areas we focus on along with power management, data conversion, and IC health and monitoring, which is why it is more important than the volume business.”
 If you enjoyed this article, you will like the following ones: don't miss them by subscribing to :
eeNews on Google News
If you enjoyed this article, you will like the following ones: don't miss them by subscribing to :
eeNews on Google News